Next stop for Bond is Shanghai. The Chinese city the actual night was a magnificent backdrop to his mission, as he follows the enemy for this airport to some skyscraper. His stealth will be compromised as he has to jump and cling on to the elevator that goes substantially as dizzying heights. He clearly is not inside his prime and struggles carry out. There is a close fight between him and the enemy agent, who falls to his death without giving Bond the desired information. When Bond investigates the case of his enemy’s gun he finds an intricate dragon engraved on a texas holdem chip.
Despite the variety times internet security software experts warn victims in regards to dire threats of online attacks, many consumers still don’t obtain the message. Most of the is, might possibly happen to anybody – including Your. Therefore, I have decided take a look at a ‘reverse psychology’ approach in hopes that much more users think about their cyber safety.
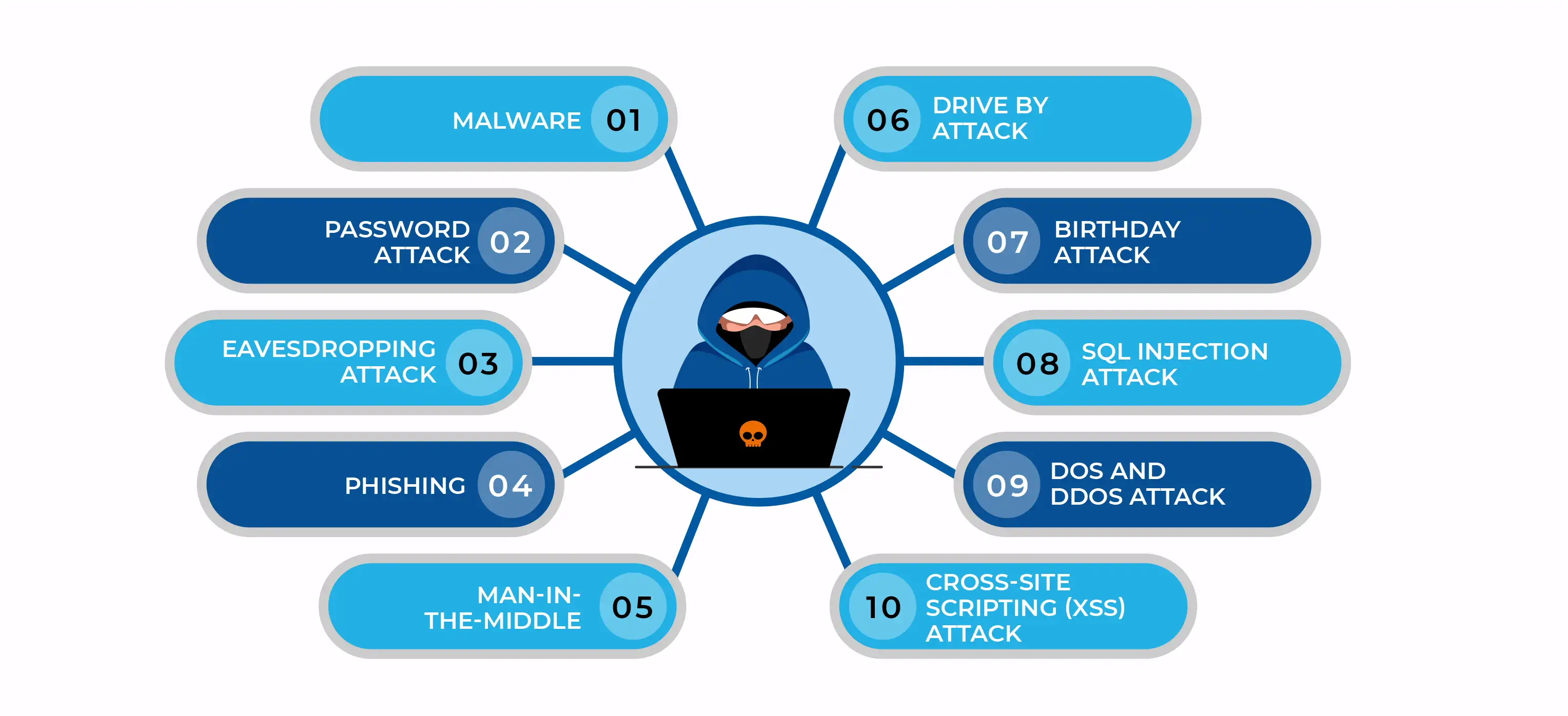
Now, altering the technical side. Number of obvious number of types of hacking. Here are some only concentrate ourselves to internet hacking which involve ordinary everyday people. What an ordinary person might wear internet? Two things: Email accounts and online sites kinds. He has most personal data in 2 places inside this device . where his privacy becomes vulnerable. If he unfortunately has some acquaintance will be not a positive person and possess sound knowledge of internet, then that person might face consequences some where in upcoming months or years.
What’s the likelihood of either scenario ever developing? Between non-existent to highly probable. We live in the world where absolutes mean nothing as each day passes and we surpass what was previously thought impossible.
Protect your hard drive by clients that could updated. Required to antivirus computer program as appropriately. This will avoid Cyber Attacks . Beware when downloading files or installing programs, because among them could include spywares. Another approach to protect your computer is the a password that only you know.
Keep in your that a high quality security awareness program can be a program that is recommended you have for keeps. You have probably heard me mention that business security is not merely a destination, accredited lifelong program. The need will never go over.
Put simply cyber stalking is where an offender, let’s phone them Mr Any kind of a. Creep uses technology for instance facebook, email or mobile handsets to stalk you. Mr A. Creep as a cyber stalker wont stalk you when you’re going into the shops or out with friends, having said that they will stalk you when you are net. Research suggests that this can help curb still cause serious psychological damage and it a significant problem.
Many of them are crossing the borders into kinds of web-sites including industry website forums and information sites. The influx of the illegal bloggers and Sploggers is increasing at a quick rate. Cyber tribalism and cyber bullying is also on an upswing on blogs across our nation device must finished.